Hackers for hire targeted 3ds Max, Bitdefender warns
Autodesk’s advisory for the PhysXPluginMfx exploit, which cybersecurity firm Bitdefender believes has been used for corporate espionage in the property industry. Autodesk has released tools to remove the malware.
Cybersecurity firm Bitdefender has published a report on a new script exploit in 3ds Max, saying that it appears to be the result of an international hacker-for-hire group.
Bitdefender described the exploit as a “sophisticated APT-style cyberespionage attack”, and speculates that a property firm may have used hackers to spy on competitors by targeting contractors using 3ds Max.
Autodesk had already identified the PhysXPluginMfx exploit, which affects 3ds Max 2015 to 2020, and has updated its free Security Tools for 3ds Max software to fix the vulnerability.
Download and run Autodesk’s Security Tools to remove this and other malware
Security vulnerabilities in 3ds Max – or any other software – are not uncommon: Autodesk has published three security advisories on exploits in 3ds Max and Maya that it regards as of “high” severity this year.
In the case of PhysXPluginMfx, Autodesk published an advisory on the MAXScript exploit on 10 August.
According to Autodesk, the malware can corrupt “[software] settings, run malicious code, and propagate to other MAX files (*.max) on a Windows system if scene files containing [it] are loaded into 3ds Max”.
Security Tools for 3ds Max was updated at the time, and has been further updated since, so if you’re a Max user, download it from the Autodesk App Store to close this and other vulnerabilities.
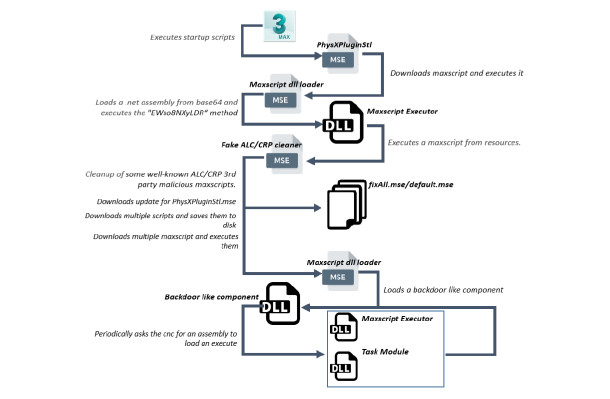
How the PhysXPluginMfx exploit is used. Diagram from Bitdefender’s white paper.
Exploited for industrial espionage in the property industry, Bitdefender believes
What’s interesting about the Bitdefender report is that it suggests that the exploit is the result of industrial espionage in the real estate market, using a hacker-for-hire group to target 3ds Max.
According to Bitdefender, it “recently investigated an APT-style [Advanced Persistent Threat] cyberspionage attack targeting an international architectural and video production company”.
The targeted company is not named, but is “known to have been collaborating in billion-dollar real estate projects in New York, London, Australia, and Oman”.
Bitdefender researchers “found that threat actors had an entire toolset featuring powerful spying capabilities”, making use of the previously unknown vulnerability in 3ds Max to “compromise the target”.
The firm comments that “the commoditization of APT-level hackers-for-hire could potentially entice luxury real-estate investors … to seek these services to spy on their competition by infiltrating their contractors”.
Bitdefender said that the command and control server used in the attack was located in South Korea, and that it believes that other firms throughout the world will have been similarly affected.
“Based on Bitdefender’s telemetry, we also found other similar malware samples communicating with the same command and control server, dating back to just under a month ago.
“Located in South Korea, United States, Japan, and South Africa, it’s likely the cybercriminal group might have also been targeting select victims in these regions as well.”
Read more about Bitdefender’s investigation on its website
Read Autodesk’s security advisory on the PhysXPluginMfx exploit
Download Autodesk’s free Security Tools for 3ds Max
(Compatible with 3ds Max 2015 SP1 to 3ds Max 2021)
